Malware traffic analysis can initially feel overwhelming, with the sheer volume of data in packet captures making it challenging to know where to start. This post is designed to simplify the process, guiding you through setting up Wireshark, analysing a sample packet capture, and extracting actionable insights—skills essential for blue teams and security analysts alike.
While I’m no expert, I am confident that by following along you’ll gain insight into this process to help get you started in this sort of work.
Drawing inspiration from Brad Duncan’s excellent resources at www.malware-traffic-analysis.net, we’ll work through the foundational concepts using his 2019-11-12 exercise, “Okay-Boomer.” Learn with me and hopefully by the end of this post, you’ll have the confidence to approach similar exercises and apply these techniques to real-world scenarios.
What You’ll Learn
- Configuring Wireshark for effective traffic analysis
- Identifying user agents to determine device types and operating systems
- Locating MAC addresses and associating them with manufacturers
- Extracting usernames from Kerberos traffic
- Recognising suspicious file downloads and generating their hashes
Let’s get started.
Setting Up Wireshark
Before analysing traffic, we’ll configure Wireshark for optimal use. Brad Duncan’s video tutorials are an excellent starting point, walking through the setup process step by step. Proper configuration not only streamlines analysis but also ensures consistency across exercises and real-world tasks.
Once configured, download the “Okay-Boomer” packet capture from Brad’s website and extract it using the password provided on the About page. Open the file in Wireshark to begin your exploration.
Hands-On Analysis
With Wireshark ready, we’ll start analysing the packet capture file to answer the exercise questions. Below, I’ll outline the steps I took to find the answers, along with the results. If you’d like to try solving the questions yourself first, feel free to do so. If you get stuck, come back here for guidance.
What operating system and type of device is on 10.11.11.94?
To determine a device’s operating system and type, we look for its user agent in HTTP traffic. While not always reliable, this is a useful method.
In Wireshark, use this filter to isolate the relevant HTTP traffic:
http.request and !(ssdp) and ip.addr eq 10.11.11.94
Then, right-click an HTTP request and select Follow > TCP Stream. The user agent will be near the top of the stream. For this packet, the user agent is:
Mozilla/5.0 (X11; CrOS x86_64 12239.92.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.136 Safari/537.36.
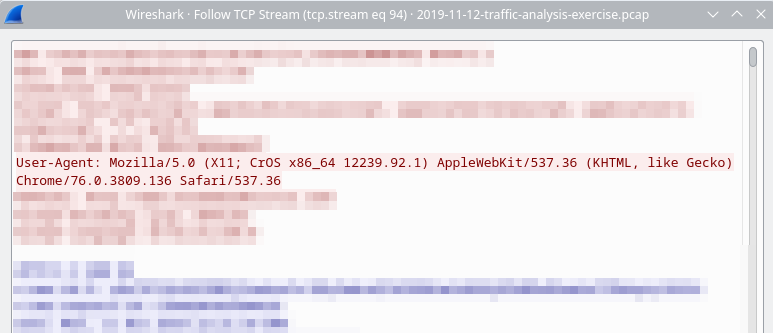
To identify the operating system and device type from the user agent, simply look it up online. This user agent indicates the device is a Chromebook running ChromeOS.
What operating system and type of device is on 10.11.11.121?
Use the same method as before with this filter:
http.request and !(ssdp) and ip.addr eq 10.11.11.121
Follow the TCP stream and identify the user agent:
Mozilla/5.0 (Linux; Android 9; SAMSUNG SM-N950U) AppleWebKit/537.36 (KHTML, like Gecko) SamsungBrowser/10.1 Chrome/71.0.3578.99 Mobile Safari/537.36.
A quick search shows this device is a Galaxy Note 8 running Android.
Based on the MAC address for 10.11.11.145, who is the manufacturer or vendor?
In Wireshark, you can find the MAC address in the Ethernet II section of the packet details. Use this filter to focus on the relevant IP address:
ip.addr eq 10.11.11.145
Select one of the entries to view the Ethernet II details:
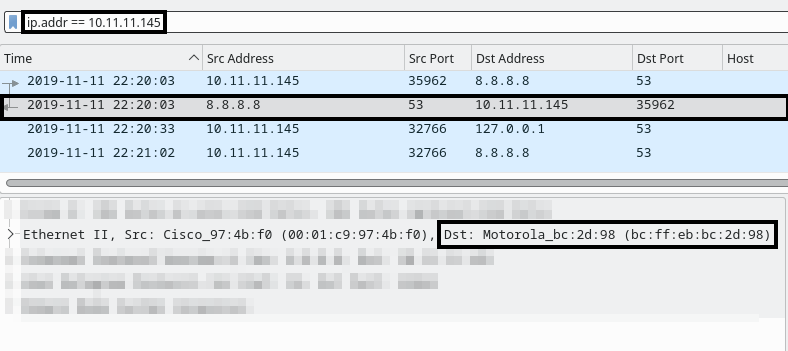
The MAC address shows that the manufacturer is Motorola.
What operating system and type of device is on 10.11.11.179?
Use the same method as previous questions to find the user agent for this IP. The user agent is:
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_1) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/13.0.3 Safari/605.1.15
This indicates a Mac running MacOS 10.15.1.
What version of Windows is being used on the host at 10.11.11.195?
Again, filter for HTTP traffic and follow the TCP stream to identify the user agent:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.102 Safari/537.36 Edge/18.18362.
The user agent indicates the device is running Windows 10.
What is the user account name used to log into the Windows host at 10.11.11.200?
Kerberos traffic provides a straightforward way to find usernames. Filter for Kerberos traffic:
kerberos.CNameString and ip.addr eq 10.11.11.200.
From here, the easiest way forward is to find a packet with this field somewhere in the Kerberos section in the packet details area. Select a few packets until you find one that lists this (you’ll need to expand the following items to find it: Kerberos > tgs-rep > cname > cname-string). Once there, right click the CNameString listed and select Apply as Column.
You may have already seen the answer to this question when creating the column, but adding this column makes it easier to find this information in the future if you need to. In this case, we can look through the traffic, and our new column, to identify the user as brandon.gilbert:
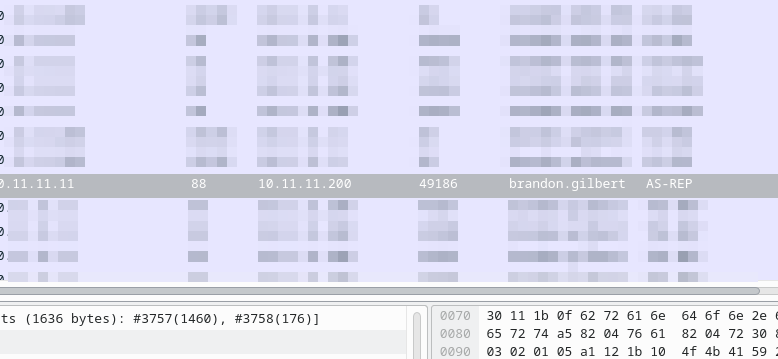
What operating system and type of device is on 10.11.11.217?
Use the same steps from earlier to find the user agent for this IP:
Mozilla/5.0 (iPad; CPU OS 13_2_2 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/13.0.3 Mobile/15E148 Safari/604.1
This user agent identifies the device as an iPad running iPadOS 13.2.2.
What IP is the Windows host that downloaded a Windows executable file over HTTP?
To identify Windows executables, filter for the string:
ip contains "This program".
This should return a single packet. Looking at the packet bytes we can immediately see the string we were looking for, as well as another handy piece of text:
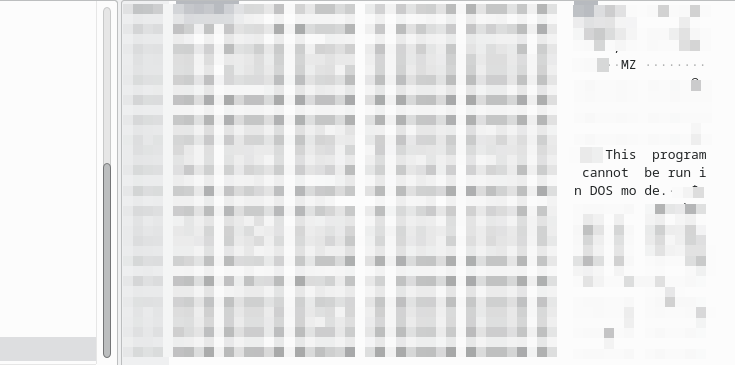
We can see here the characters ‘MZ’, which are the first two bytes for a Windows DLL or executable file. Additionally, we see the string we filtered for, “This program cannot be run in DOS mode” which is also commonly found in these file types.
So, we’ve identified the only download of a Windows executable in the packet capture, what is the IP address of the host that downloaded it? Well, it’s the only one listed when we use our filter from above: 10.11.11.203,
What is the URL that returned the Windows executable file?
If we follow the TCP stream for the packet in our previous filter (and close the TCP stream window) we can look through the list to find the GET request that downloaded the file. In this case, we can see the host name listed as acjabogados.com and the path of /40group.tff.
What is the SHA256 file hash for that Windows executable file?
In order to get the has of a file or object in a packet capture in Wireshark we need to export the object and save it to our computer for hashing.
To do this, go to File > Export Objects > HTTP and locate the file you’re wanting to hash. In this case, we’ve already identified that the file we want is an image/tiff file downloaded from acjabogados.com. So, locate that in the list of objects, select it and hit Save.
There are a heap of different ways to find the hash of a given file, but the one that I use most commonly is done through a terminal on Linux. If you’re using Linux, you can open a terminal in the folder where the file is stored and run sha25sum 40group.tiff in order to generate a SHA256 hash of the file we just saved. If you’re using another device, you may want to use a similar method (ie. through PowerShell on Windows) or simply use an online tool for this.
The hash for this file is: 18d5d36c8ffb0a9c81b145aa40c1ff3475702fb0b5f9e08e0577bdc405087e635.
What is the detection rate for that SHA256 hash on VirusTotal?
Search the hash on VirusTotal. As of writing, 58/71 security vendors and 1 sandbox flagged the file hash as malicious.
What public IP addresses did that Windows host attempt to connect over TCP after the executable file was downloaded?
I wasn’t able to answer this question myself, but the solution given by Brad for this question was to use a filter like this:
(http.request or tls.handshake.type eq 1 or tcp.flags eq 0x0002) and !(ssdp) and ip.addr eq 10.11.11.203 and !(ip.dst eq 10.11.11.11)
And look for the failed packets in the results, which we can see in this screenshot:
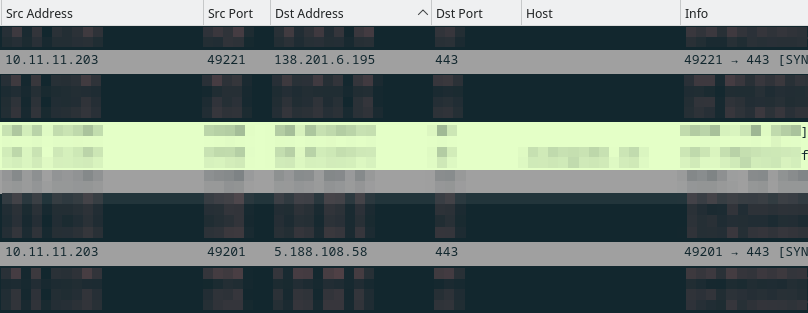
This reveals the IPs: 138.201.6.195 and 5.188.108.58.
What is the host name and Windows user account name used on that IP address?
The IP address for the host listed previously is 10.11.11.203, so we can use our method of filtering for Kerberos traffic and finding the CNameString column from earlier to find the answers to this question.
The filter I used was just kerberos and ip.addr eq 10.11.11.203. With the CNameString column still applied from earlier, a quick glance over traffic in this filter reveals the username as candice.tucker and the host name as TUCKER-WIN7-PC.
Conclusion
Malware traffic analysis is a crucial skill for anyone working in defensive security. By examining packet captures in Wireshark, you can identify malicious activity, understand attack patterns, and gather vital information for threat mitigation. The techniques demonstrated in this guide, such as identifying user agents, analyzing Kerberos traffic, and extracting file hashes are foundational to successful traffic analysis.
With practice, these skills will become second nature, helping you to detect threats early and respond swiftly. Whether you’re learning through exercises like “Okay-Boomer” or analyzing real-world captures, mastering malware traffic analysis is an essential step in building a solid cybersecurity foundation.