This post looks how to analyse a packet capture file in Wireshark, identfying relevant pieces of information from the perspective of a blue team or security analyst.
When I first started learning about traffic analysis and working with Wireshark I found the amount of information available overwhelming, which made the task of learning about this new area of interest a little more daunting than it ought to be.
Fortunately, there are a heap of really good resources available online for learning about this process, one of them being Brad Duncan’s various tutorials, blog posts and exercises, most of which are available on his website, www.malware-traffic-analysis.net.
One of the exercises on the site, from 2019-11-12, titled ‘Okay-Boomer’ is a great place to start for anyone new to traffic analysis of this kind. The exercise and questions are both simple and interesting enough that they serve as a good introduction to this sort of process. In this post, I want to go through the process I followed to get Wireshark set up for traffic analysis, download the packet capture, open it in Wireshark and answer each of the questions that Brad poses for this particular exercise.
My hope is that by the end of reading through this post, assuming that you follow along and try out each of the methods below, that a beginner to malware traffic analysis, or just Wireshark in general, will have a solid foundation from which they can begin using Wireshark.
In this post you’ll learn how to:
- Set up and configure Wireshark for traffic analysis
- Use Wireshark to find the user agent of a given device for a specific IP address, and identify its operating system and device type
- Find the MAC address for a device given a specific IP address in Wireshark
- Find user account names and host names through Kerberos traffic in Wireshark
- Identify downloads in Wireshark traffic, and create a hash for those files
- And maybe a few other things!
Initial setup and configuration
While we don’t technically need to do much to get Wireshark ready for this exercise, it is a good idea to follow Brad’s guide to configuring and setting up Wireshark anyway, as it will create a solid foundation for your future work with Wireshark. You can watch that video workshop on setting up Wireshark on YouTube.
Once you’ve got Wireshark set up, you can download the packet capture file from Brad’s website. You’ll need to extract the file from a password protected archive (you can find the password on the ‘about’ page of the Malware Traffic Analysis website). From there, open up Wireshark, navigate to File > Open and select the packet capture file to get started.
Working through the exercise and answering the questions
Now that we have Wireshark set up and ready to work with us we can begin looking at the traffic in the packet capture file to start answering the questions for the exercise. I’ll outline the method I used for finding the answer, as well as provide the answers for each question. If you’d like to have a go at answering the questions on your own first then now is the time to do that. If you get stuck, you can revisit this post for help.
What operating system and type of device is on 10.11.11.94?
One way to find a device’s operating system and device type is by finding the user agent that it is using. While not always reliable, it’s one of the few methods that we have for answering this question. User agents can be found rather simply in HTTP traffic, which is what we’ll use to answer this question.
In Wireshark, filter for HTTP traffic and the relevant IP address by using the following filter:
http.request and !(ssdp) and ip.addr eq 10.11.11.94
Once filtered, select a HTTP request from the traffic and right click it, selecting Follow > TCP Stream. A window should open showing you that packets TCP stream. The user agent will generally be listed toward the top of the displayed text. The user agent for this particular packet is listed as Mozilla/5.0 (X11; CrOS x86_64 12239.92.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.136 Safari/537.36.
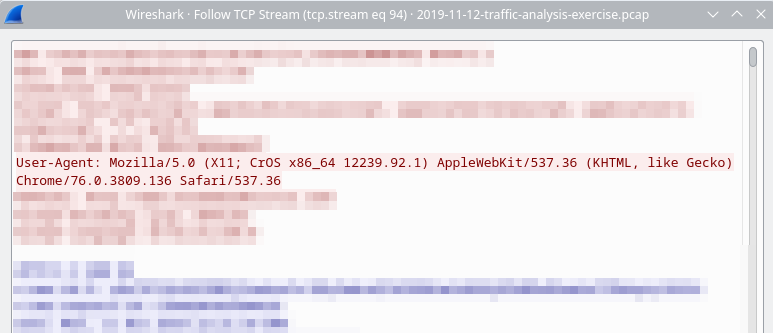
To identify the operating system and device type from the user agent, simply look it up online. In this case, the user agent relates to a Chromebook running ChromeOS.
What operating system and type of device is on 10.11.11.121?
In this case we can use the method from the above question to obtain the operating system and device type on this IP address. Using the same filter from earlier, but changing the IP address (``http.request and !(ssdp) and ip.addr eq 10.11.11.121`) filters the packets down to only show HTTP traffic for this IP address. Just like before, if we follow a TCP stream for a HTTP request we can identify the user agent.
In this case, the user agent is listed as Mozilla/5.0 (Linux; Android 9; SAMSUNG SM-N950U) AppleWebKit/537.36 (KHTML, like Gecko) SamsungBrowser/10.1 Chrome/71.0.3578.99 Mobile Safari/537.36. A quick search online indicates that this device is operating a Galaxy Note 8 running Android as its operating system.
Based on the MAC address for 10.11.11.145, who is the manufacturer or vendor?
We can find a MAC address in a few different ways, but one of the simplest is to simply look under the packet details section at the Ethernet II option.
In this case we’re looking for the manufacturer or vendor for a specific device based on an IP address, so we can start by filtering the traffic for that address specifically. You should be used to what these filters look like by now:
ip.addr eq 10.11.11.145
Once we’ve filtered the traffic we can simply select one of the entries to view the Ethernet II details mentioned above:
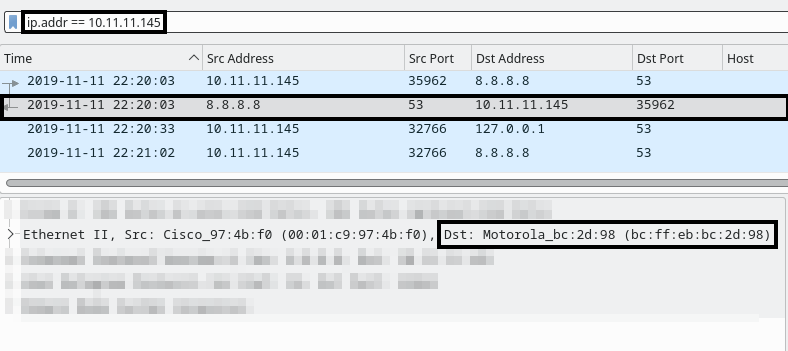
In this case, we don’t need to do any further searching or research, as we can see from the MAC address that Motorola is the manufacturer.
What operating system and type of device is on 10.11.11.179?
Are you getting tired of following TCP streams yet? I hope not! We’ll use the same method from questions one and two to find the operating system and device type for this IP address, but I won’t walk through this again, simply refer to those questions for the method, write a new filter for this IP address and identify the user agent. If your approach is correct, you should find Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_1) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/13.0.3 Safari/605.1.15, which relates to a device using MacOS (10.15.1) on a Mac computer.
What version of Windows is being used on the host at 10.11.11.195?
If you saw this question and guessed that we might find this by looking for a user agent, then you’d be correct. Let’s filter for HTTP traffic on this IP address as we’ve done earlier using http.request and !(ssdp) and ip.addr eq 10.11.11.195 and follow the TCP stream for one of the HTTP requests.
The user agent listed for this particular device is Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.102 Safari/537.36 Edge/18.18362. If you ever see Windows NT 10.0 listed in a user agent string, you can safely bet that this is a device running Windows 10, which is the answer to this question.
What is the user account name used to log into the Windows host at 10.11.11.200?
If your packet capture has Kerberos traffic in it you can usually find the usernames and other information quite easily (so it’s usually a nice relief when this is present in a capture, like it is for this exercise).
We can filter for Kerberos traffic easily by just typing kerberos into the filter. For this question, we’re looking for the username specifically, which is found as a CNameString in Kerberos traffic, so we’ll filter for that. We’ll also want to hone in on the IP address in the question, so we’ll use a similar filter to what we have already: kerberos.CNameString and ip.addr eq 10.11.11.200.
From here, the easiest way forward is to find a packet with this field somewhere in the Kerberos section in the packet details area. Select a few packets until you find one that lists this (you’ll need to expand the following items to find it: Kerberos > tgs-rep > cname > cname-string). Once there, right click the CNameString listed and select Apply as Column.
You may have already seen the answer to this question when creating the column, but adding this column makes it easier to find this information in the future if you need to. In this case, we can look through the traffic, and our new column, to identify the user as brandon.gilbert:
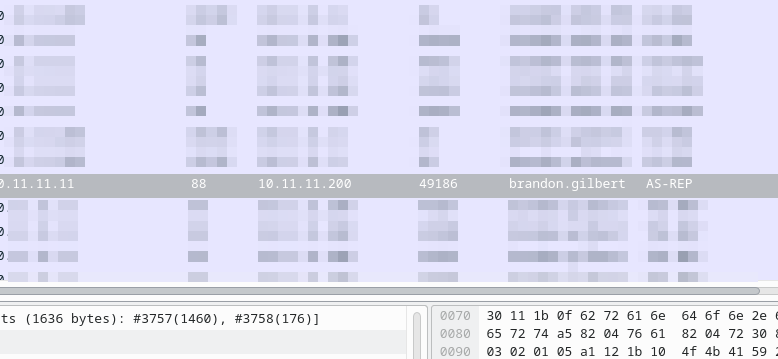
What operating system and type of device is on 10.11.11.217?
Once again we find ourselves following TCP streams and hunting down user agents. Follow the steps from one of the earlier questions of the same nature to generate a filter for honing in on traffic relevant to this IP address and identify the user agent in order to find the operating system and device operating on that IP.
In this case, the user agent is Mozilla/5.0 (iPad; CPU OS 13_2_2 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/13.0.3 Mobile/15E148 Safari/604.1 which a quick search online identifies as an iPad running iPadOS 13.2.2.
What IP is the Windows host that downloaded a Windows executable file over HTTP?
There are a few different ways to find the answer to this question (how to find executables downloaded in a packet capture in Wireshark). A method that works for looking for Windows executables in particular is to filter the traffic for a string commonly found in Windows executable files: ip contains "This program". This should return a single packet.
Looking at the packet bytes we can immediately see the string we were looking for, as well as another handy piece of text:
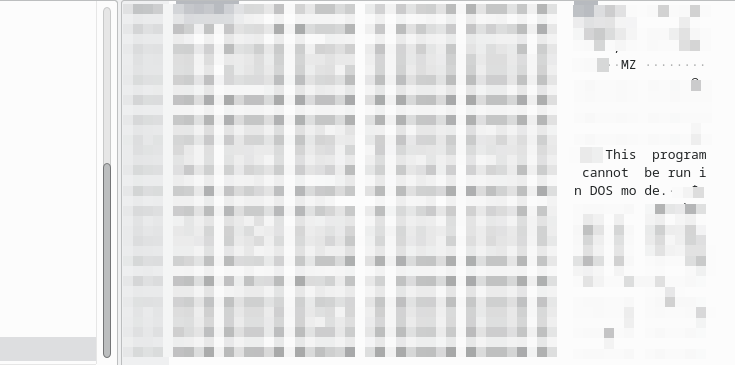
We can see here the characters ‘MZ’, which are the first two bytes for a Windows DLL or executable file. Additionally, we see the string we filtered for, “This program cannot be run in DOS mode” which is also commonly found in these file types.
So, we’ve identified the only download of a Windows executable in the packet capture, what is the IP address of the host that downloaded it? Well, it’s the only one listed when we use our filter from above: 10.11.11.203,
What is the URL that returned the Windows executable file?
If we follow the TCP stream for the packet in our previous filter (and close the TCP stream window) we can look through the list to find the GET request that downloaded the file. In this case, we can see the host name listed as acjabogados.com and the path of /40group.tff.
What is the SHA256 file hash for that Windows executable file?
In order to get the has of a file or object in a packet capture in Wireshark we need to export the object and save it to our computer for hashing.
To do this, go to File > Export Objects > HTTP and locate the file you’re wanting to hash. In this case, we’ve already identified that the file we want is an image/tiff file downloaded from acjabogados.com. So, locate that in the list of objects, select it and hit Save.
There are a heap of different ways to find the hash of a given file, but the one that I use most commonly is done through a terminal on Linux. If you’re using Linux, you can open a terminal in the folder where the file is stored and run sha25sum 40group.tiff in order to generate a SHA256 hash of the file we just saved. If you’re using another device, you may want to use a similar method (ie. through PowerShell on Windows) or simply use an online tool for this.
The file hash that should be returned no matter what method you use is 8d5d36c8ffb0a9c81b145aa40c1ff3475702fb0b5f9e08e0577bdc405087e635, which is also the answer to this question.
What is the detection rate for that SHA256 hash on VirusTotal?
Now that we have the file hash we can easily search for it on platforms like VirusTotal, which is an online platform used to analyse files, domains, IP addresses and in this case, file hashes, in order to detect malware and other security breaches or flaws.
To do this, open VirusTotal in your browser, navigate to the Search option and paste in our SHA256 hash.
The answer to this question will likely change over time, but as of the time of writing 58/71 security vendors and 1 sandbox flagged the file hash as malicious.
What public IP addresses did that Windows host attempt to connect over TCP after the executable file was downloaded?
I wasn’t able to answer this question myself, but the solution given by Brad for this question was to use a filter like this:
(http.request or tls.handshake.type eq 1 or tcp.flags eq 0x0002) and !(ssdp) and ip.addr eq 10.11.11.203 and !(ip.dst eq 10.11.11.11)
And look for the failed packets in the results, which we can see in this screenshot:
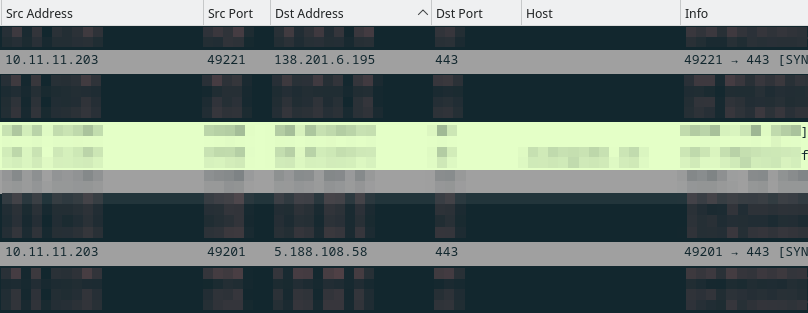
They are 138.201.6.195 and 5.188.108.58.
What is the host name and Windows user account name used on that IP address?
The IP address for the host listed previously is 10.11.11.203, so we can use our method of filtering for Kerberos traffic and finding the CNameString column from earlier to find the answers to this question.
The filter I used was just kerberos and ip.addr eq 10.11.11.203. With the CNameString column still applied from earlier, a quick glance over traffic in this filter reveals the username as candice.tucker and the host name as TUCKER-WIN7-PC.
Conclusion
Thanks for reading through this write up and guide. I hope that it helped in some way. All of this information and knowledge was more or less sourced and learnt from Brad Duncan, his work on the Malware Traffic Analysis website or his guides written for Unit-42, so I’d like to extend a massive thank you to him for making all of this available to anyone to learn for free.
If you’d like to continue learning more about this topic then I cannot recommend his work more.